One of our clients decided to host their website on Weebly. Our experience has been to let people follow the instructions on the websites of people like Weebly, Wix, WordPress.com, etc., to use their nameservers under a number of understandings:
- Such web-building websites claim that they need the ability to change the IP address of the user’s website at short and/or unannounced notice, and giving them control of the nameservers allows them to do this to minimise downtime, and
- They give the client control over their nameservers under a control panel, so that the clients can add and manage nameserver records at will.
Unfortunately, as of this month (December 2025), Weebly’s nameserver controls were not working. Nameservers are used for a number of routine and esoteric purposes; you can, for example, create a TXT record that says, “Hello world!”, which does nothing but say hello! 🙂 One of the suppliers of a few of our clients actually does this on one of their domains, if you can believe that:
user@machine:~$ dig +short txt resrequest.co.za
“Hello world!”
user@machine:~$
They don’t even create a TXT record that does anything useful, like direct users to the TXT record of resrequest.COM for useful information about a secondary domain that they use in certain circumstances.
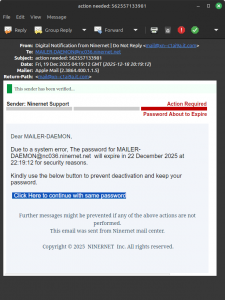
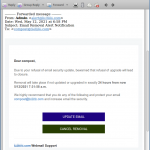
Anyway, one of the more routine reasons to create any kind of record is to show certain information to other users (which include people and machines) for the purposes of authentication, which is why some organisations have you create TXT records like “google-site-verification=y0se7y0r7ygncCNYW0RE09T078989c90nmt89cnsygf”. But if you have no control over your DNS — which was the case with our client — you can’t create such a record, and so you can’t authenticate yourself with Google. In our case the client couldn’t create two CNAME records which are required by the email system to authenticate your domain. The Weebly control panel seems to provide this functionality, but it doesn’t work; the records you create do not exist in the DNS, and they don’t even appear in the control panel. Since the domain was created through the Weebly system, access to configure the domain wasn’t available through the registrar, so we had to transfer it immediately to take control so that we could create the necessary CNAMEs. Now the domain does not use Weebly’s nameservers, which means that their website could be down one day if Weebly chooses to change its IP address, but their email was down for a week or two because they couldn’t create the two necessary CNAMEs.
So it depends what’s more important to you: your website or your email. Weebly has demonstrated their incompetence not only by having a control panel that doesn’t work, but by their support personnel giving our client an absolutely BS excuse that reminded me of another client being told years go that something he was trying to do wouldn’t work because “the Internet was down”! The Internet was down! The whole Internet! My god. In this case the client was told that something completely unrelated (the DNS) was broken because someone sent a plain-text email. I can’t even connect the dots on that one because the dots are all over the place; there is no way that sending a plain-text (or even HTML-formatted email) can affect the DNS, as the two systems are not connected, related or affected by the information in one system affecting the other. Maybe the information was relayed to me incorrectly, but to me this sounds exactly like someone trying to baffle the client with BS.
So, in the future, we will advise clients using Weebly not to use their nameservers, but to use ours, where they have working control over the DNS for their domain.