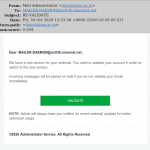
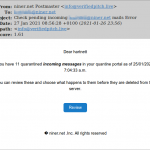
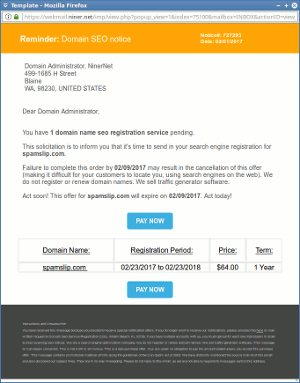
Scam and “phishing” emails arrive daily by the truck load. We can’t send a warning every time we ourselves get a scam or phishing email. If we did, our own emails would become just noise in the background.
However, we present here eighteen screenshots of scam, spam and phishing emails that we have received or seen over the last four years. If you’re not sure what one of these emails look like, we encourage you to look these over. The approaches vary, but here are some common factors:
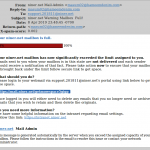
- They advise you that your email account is over quota, and you must take some immediate action to prevent catastrophe — i.e., the loss of all your email.
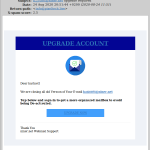
- Your email account is being closed or upgraded.
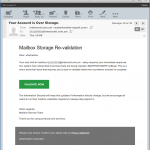
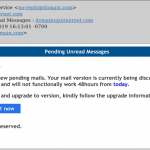
- The webmail for your account is being upgraded, and you have to take action.
- Your domain is being cancelled or expired within a few hours or a couple of days.
- Payment for the renewal of your domain is overdue.
- Wordy expiration notices that are unclear about what exactly is expiring and how it could theoretically affect you.
- Domain SEO (search engine optimisation) notices made up to look like invoices for domain renewal.
- Emails with links that disguise the true destination to which you are clicking. Always check the status bar in your email program or app — before you click, while hovering your mouse pointer over the link — to determine whether or not your browser will really be going to a domain you recognise — e.g., niner.net if you are a NinerNet Communications client.
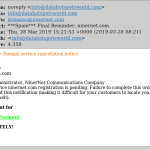
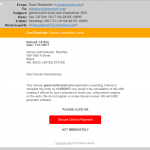
- Emails that try to sound like they come from your own company’s IT department, complete with copyright notices.
- “Final” renewal notices that are a surprise.
- Fine print at the end of the email that makes ludicrous statements that contradict the meat of the email, such as, “We do not directly register or renew domain names” or “THIS IS NOT A BILL” (in an email that looks like it’s a bill to renew your domain); “We have clearly mentioned the source mail-id of this email, also clearly mentioned our subject lines and they are in no way misleading” (in an email that tries to mislead you into paying what looks like an invoice).
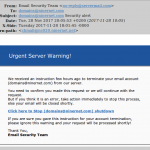
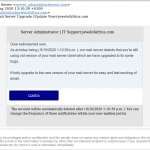
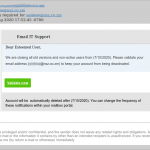
- Urgent server warnings, that aren’t urgent server warnings at all.
NinerNet Communications is judicious about how many emails we send out, and how often we do. We’re also careful to ensure that we use proper spelling and grammar. Our emails do not contain copyright notices and pages of meaningless legal notices. (Maybe they should, but currently they don’t. We’re real people who tend to believe that our clients are also real people with brains.) With that in mind, here is a non-exhaustive list of things you should look for to determine if an email you’ve received really is from NinerNet and if it’s legitimate:
- Is it from an email address on the niner.net domain? (Configure your email program or app to show you the sender’s actual email address, not just their name.) If it’s not, it’s not from us and you can probably ignore it if it claims to be about your hosting or domain.
- Does it try to scare you or make you angry, such that you might take immediate action? If it does, it’s definitely not from us.
- Is it in HTML or “rich text”, with different colours and types of fonts, and does it contain images or things that look like buttons (especially that say “secure online payment”)? It’s very likely not from us.
- Are there copyright notices in the email? Definitely not from us.
- Does it flatter you with words such as “esteemed” or “valued”? Not from us. (You are esteemed and valued, for sure; we just don’t lay it on thick with you!)
- Does the email address you by the name in your email address? For example, if your email address is accounts@example.com, does it address you as “accounts” as if that was your name? Not from us.
- Does it ask for personal information or ask you to update or confirm personal information? Very likely not from us unless you’re a brand new client.
- Look very carefully at the sender’s address. Does the font on your email program make some letters look like others? For example, if the sender looks like bob@example.com, are you sure his domain isn’t exarnple.com? With some fonts the “r” and the “n” together look like the “m” in “example”.
Of course, the above checklist can be applied to any email you receive, including emails that purport to be from your bank.
Attachments: Don’t open attachments from unknown senders or that you are not expecting, even from known senders. Also make sure you have anti-virus software installed.
Our automated notices telling you that your mail box is full, or close to it, are extremely brief and do not try to scare you or offer you links to “free upgrades” or anything like that.
If you click on a link in an email and enter information on a form — especially a password — and then realise that it’s a scam/phishing, immediately change that password. You should also contact NinerNet, or whoever that account is with, to inform them what has happened.
Finally, when we do send you an email to advise you of something that applies to all (or most) clients — such as server moves, upgrades, etc. — we include a link to our blog (blog.niner.net) so that you can confirm that information.
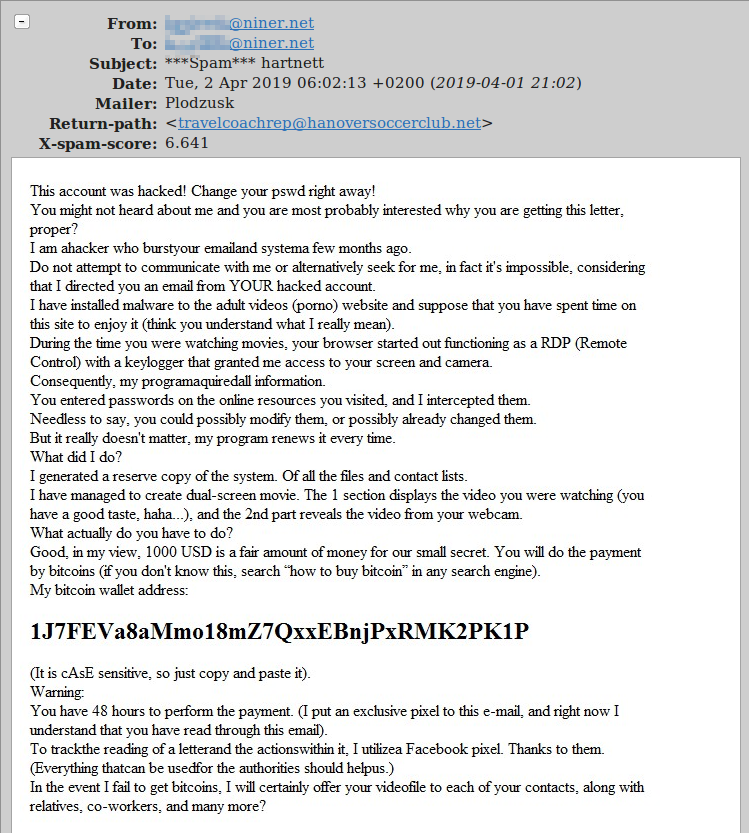
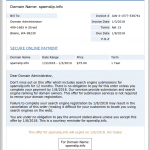
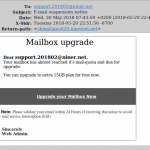
Below, then, are the eighteen screenshots of scam, spam and phishing emails. The first is particularly noteworthy, as it is a sexual blackmail/extortion scam that seeks payment via Bitcoin. It and similar emails will be the subject of our next blog post.
If you have any questions, please contact NinerNet support. Thank-you.
- Urgent server warning email scam.
- Mailbox over storage revalidation email scam.
- Mailbox is full email scam.
- Using old version email scam.
- Important domain seo notification email scam.
- Domain service cancellation scam.
- Upgrade account email scam.
- Secure online payment email scam.
- Domain service cancellation scam.
- Domain danger suspended scam.
- Pending unread messages email scam.
- Notice of final renewal domain scam.
- Domain cancellation notice scam.
- Closing old versions email scam.
- Mailbox upgrade quota email scam.
- New version webmail email scam.
- Check pending incoming email scam.