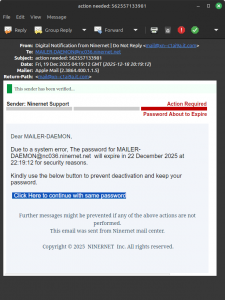
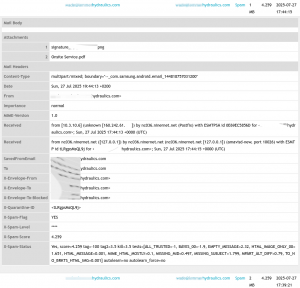
For some time now the main registrar we use has been masking domain ownership in the WHOIS and providing a default email address for all registrants on the domain-contact.org domain. They provide a contact form on that domain as well. However, spammers have been using that form to spam because, apparently, Centralnic doesn’t care to protect registrants from spam and therefore protect it from automated submissions.
So we are adding domain-contact.org to the spam filter. This will send all email from that domain to the quarantine.
If, for some bizarre reason, you count on contact from that form — which, in thirty years, we think nobody ever does or has — please contact us to advise us, or know that you need to check your quarantine on a regular basis.