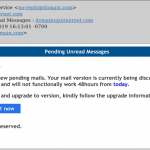
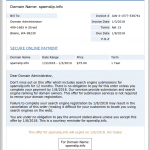
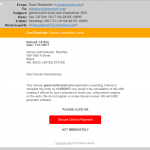
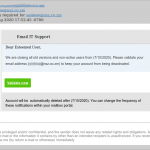
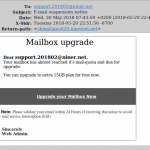
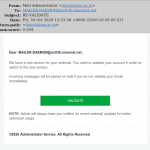
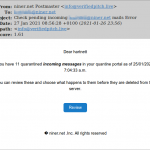
Please be advised that there is a phishing message getting through the spam filters with the subject:
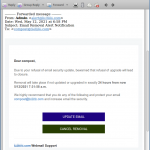
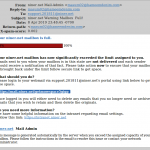
Oops, Error updating the POP/IMAP server of YOUR-DOMAIN.TLD
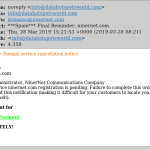
In the actual email, “YOUR-DOMAIN.TLD” just happens to be the domain of the email address to which the scam was sent (see screenshot below). (What a coincidence!) These are not sent by NinerNet, as even a cursory look at the “From” field will show. We also do not use folksy words like “Oops” in business and technical emails, and we don’t pose as the “webmaster” of your domain. We are NinerNet, and that is how we always present ourselves to you, our client.
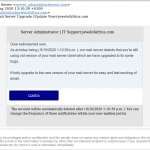
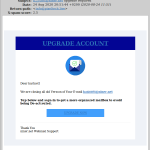
If you click the button to “Update Preferences” (or whatever action your copy of the message urges you to take) — which we strongly urge you not to do! — you will be taken to a page that looks like the log-in page for a webmail system (not our webmail system, I hasten to emphasise!), where the scammers expect that you will enter your email log-in information. Your log-in will fail, of course, but you will have given your real email password to the scammer, who will then use it to hijack your account.
If you or someone in your organisation falls for this, change the password for that account immediately! It’s not shameful to fall for a scam; many are convincing and we are all busy people who sometimes do something we regret when we are busy and distracted. What is important is that you recognise what has happened and take action to prevent any further damage.
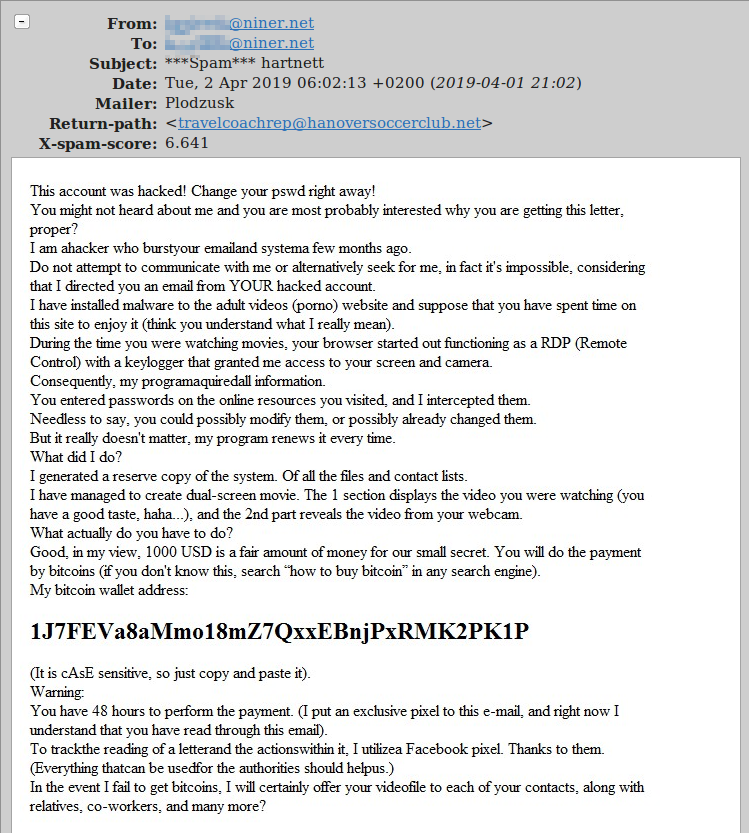
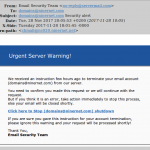
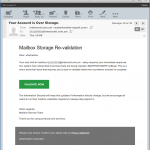
Please be aware of and do not fall for these types of messages! The spam filter has been catching a lot of these types of messages lately, but the casual language of this one seems to be defeating our spam filters.
Please ensure that your employees, colleagues and other associates know about these scam messages. You should also remind yourself and your employees, colleagues and associates of the information on our website at the following links:
Thank-you for your time and attention to this vitally important matter. Please contact NinerNet if you have any questions.

Phishing scam email, 2024-05-16.